cPanel pricing increase for 2024

Starting from January 1st, 2024, we will update the pricing of cPanel licenses offered alongside our VPS plans. Below you will find the new prices applicable after this date.
Continue reading
Starting from January 1st, 2024, we will update the pricing of cPanel licenses offered alongside our VPS plans. Below you will find the new prices applicable after this date.
Continue readingDebian 12 “bookworm” was released on June 10th and is now available in the IntoVPS cloud.

Today we’re announcing a new 1 GB VPS package, we’re doubling the cores on the small packages and we’re updating our price list.

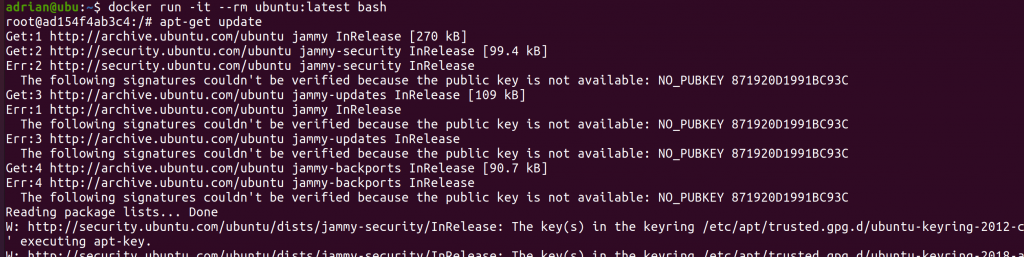
They say it’s always a good idea to pin your dependency versions to specific versions and not use things like “:latest” as base docker image or just a major version in your Python’s requirements.txt.
But why is that exactly? And what happens if you don’t do it?

Effective from the 1st of January 2022, we will adjust the pricing for cPanel licenses and VPSes with Windows operating systems.
Continue readingDebian version 11 was released on August 14th 2021:
“After 2 years, 1 month, and 9 days of development, the Debian project is proud to present its new stable version 11 (code name bullseye), which will be supported for the next 5 years thanks to the combined work of the Debian Security team and the Debian Long Term Support team.”
https://www.debian.org/News/2021/20210814

In the last few months, we have been preparing and testing new network equipment and a new network architecture, which brings a high redundancy level, an increased data traffic capacity and an additional protection against cyber attacks. We are about to replace the network equipment in the Bucharest data center by modern ones.

Kubernetes is an open-source container-orchestration system for automating computer application deployment, scaling and management.
Originally developed by Google, Kubernetes is now community driven and maintained by the Cloud Native Computing Foundation.
Kubernetes is now available in our Cluj region.

We’re ending the promotional price period for DirectAdmin and VPS’es from Cluj region.
Continue readingStarting from the 1st of January 2021 we will adjust cPanel license pricing.

cPanel has announced yet another pricing increase for all the license tiers.
We have updated our cPanel licenses page with the new pricing that applies from January 1st 2021.
Also, cPanel announced a new pricing called cPanel Solo, which has one account included. We are including this license in our pricing plan too.
Below are the new prices that will take effect immediately for new orders. All current licenses will be updated to the new pricing structure on 1/1/2021.
| cPanel Edition | Number of accounts | Current Price | New price |
| Admin Cloud | 5 | $16 | $18 |
| Pro Cloud | 30 | $22 | $24 |
| Plus Cloud | 50 | $32 | $35 |
| Premier cloud | 100 | $39 | $43 |
See the full cPanel VPS license pricing here.
CloudLinux pricing is also changing:
| License type | Current price | New price |
| CloudLinux with cPanel | $13 | $15 |
| CloudLinux without cPanel | $16 | $18 |